


 Certified Ethical Hacker Training Course for 2018
Certified Ethical Hacker Training Course for 2018
MP4 | Video: AVC 1280x720 | Audio: AAC 44KHz 2ch | Duration: 7.5 Hours | Lec: 113 | 937 MB
Genre: eLearning | Language: English
https://www.udemy.com/learn-ethical-hacking-from-beginner/
A Complete Package of Ethical hacking training suite-Nmap,E-mail hacking,Web server,System hacking,Botnet,Metasploit etc Welcome to our Certified Ethical Hacker Training Course for 2018 Certified Ethical Hacker is a professional certification provided by the International Council of E-Commerce Consultants (ES-Council) An ethical hacker is usually employed by an organization to penetrate networks and /or computer systems, using the same methods as a hacker. After all in order to find weaknesses he must think and act as one. An hacker may be employed so he may find and fix computer security vulnerabilities. A Certified Ethical Hacker has obtained a certification in how to look for the weaknesses and vulnerabilities in target system and use the same knowledge and tools and resolve those weaknesses. There are broadly three types of hackers that have evolved in the cyber world: White Hat Hacker: This is used to describe an ethical hacker. The term came about largely after hackers moved into consulting on network security and systems. White hat hacking entails software testing systems for security and breaches etc. Often network administrators also perform hacking on their own systems to looks for vulnerabilities. As a rule, a white hat hacker never breaks into a system he does not own or have authority to enter. They follow the ethics of hacking to the latter. Black Hat Hacker: This is used to describe a cracker or malicious hacker. Most importantly it does not apply to all computer criminals, Only network intruders and other activities that conflict with hacker ethics fall under this category. Grey Hat Hacker This is someone who can swing either way when he has breaches a system. Ether he will inform the hacked that there is a breach or he will share the information with the public. Often the grey hat hacker will breach a system because he can do it. They believe it is alright to perform the intrusion. The system of intrusion followed by the black hat and grey hat is the same, blurring the line between the two. However, what varies is the eventual outcome The following topics are covered in this course: Introduction to ethical hacking Networking Penetration Testing Foot printing and reconnaissance. Google Hacking Scanning. System Hacking Malware threats SQL Injection. Cross Site Scripting or XSS. Sniffing. Social Engineering. Denial of service Session Hijacking Penetration testing Buffer Overflow and exploit writing Cryptography Firewall and Honeypots Intrusion detection system Hacking web server Wireless hacking Reverse engineering E-mail hacking security compliance and auditing Incident Handling & Computer Forensics What is a Physical Security


DJordanMedia The Complete Editing Course Bundle Pack
2025-11-11 23:09:34

Luke Stackpoole – Photography Masterclass – Master The Art Of Photography
2025-11-11 18:14:10

77组电影外观Log/Rec709视频还原色彩分级调色Lut预设包Pixflow – Colorify Cinematic LUTs
2025-02-13 11:03:14

复古怀旧电影风格温暖色调索尼Sony S-Log3视频调色LUT预设ROMAN HENSE – LUTs 24 for Sony S-Log3
2025-02-13 11:01:09

JUAN MELARA – P6K2Alexa PowerGrade AND LUTs V2 GEN 5
2025-02-13 10:58:24
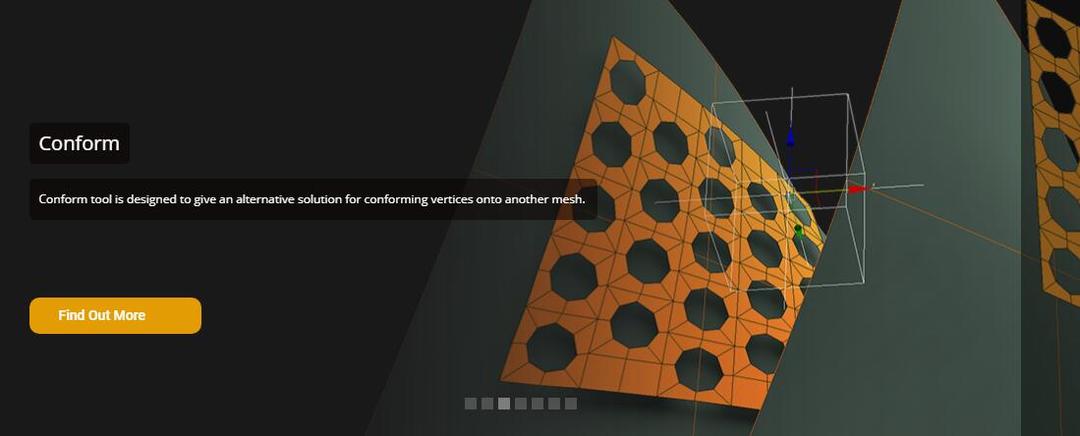
3DsMax建模插件集合:rapidTools v1.14+使用教程
2020-07-06 17:44:38

Proko-人体解剖高级付费版(中文字幕)256课
2020-12-21 18:34:01
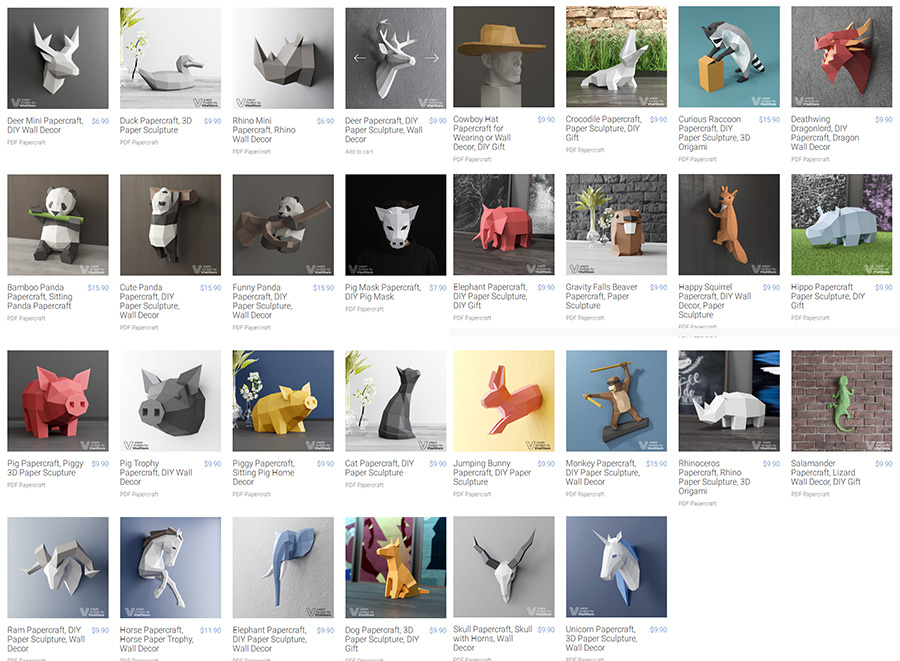
VitaliStore - All Design Bundle Papercraft Sculptures Design 动物纸模模型 纸模型雕塑设计
2020-07-21 17:18:14

小武拉莫日系摄影后期第二期中文视频教程
2021-12-10 14:26:14

Mod Portfolio 3477506 画册模板 时尚杂志画册模版
2020-07-13 10:43:06

小武拉莫日系摄影后期第二期中文视频教程
2021-12-10 14:26:14

VitaliStore - All Design Bundle Papercraft Sculptures Design 动物纸模模型 纸模型雕塑设计
2020-07-21 17:18:14

3DDD 3DSky PRO models – April 2021
2021-08-09 17:15:13

MasterClass 大师班课程84套合集+中文字幕+持续更新+赠品会员
2021-01-26 16:03:27

加特林机枪模型 加特林机关枪 Minigun Hi-Poly
2019-07-31 11:06:07





评论(0)